I had an adventure from the year 2000 to the end of 2010 that assisted tens of millions of people watch pirated TV – and almost nobody in my daily life knows anything about it.
I had an adventure from the year 2000 to the end of 2010 that assisted tens of millions of people watch pirated TV – and almost nobody in my daily life knows anything about it.
I’m seeing more and more anons come out and tell tales about their past, so I’m rather keen to relay mine before I’ve completely forgotten it. The statute of limitations on this stuff ran out this week so I feel like I am okay to talk about this now, even though technically I am still under a strict confidential agreement not to do so. For that reason I will pick my words very carefully and please don’t sue me lawyer bros!
Again the following is something I’ve never shared anywhere online, in any capacity, and this stuff happened many years ago so forgive me if I make any factual errors. I probably will. My memory is a bit fuzzy but I’ve linked to related articles to fill in the gaps.
If you were into the DSS hacking scene of the 2000’s pull up a chair and get comfy ツ

Remember when Canadians Loved Hacked American TV?
 I grew up in Canada. Due to our close proximity to the United States and dimwitted TV programming, we have a long history of hacking US television signals going back to the big C band dishes of the 1980s. I farted around with this stuff as a kid but mostly just as a channel surfer. Eventually in the 90s the dishes got smaller (D band), and cheaper but they were now properly encrypted, which slowed pirates down initially – but not for long. After a series of cards and encryption methods were cracked a wave of illegitimate satellite use in Canada followed, which eventually escalated to somewhere around ~10% of all households having h4x0red satellite TV. Yes, seriously. I knew lawyers, clergy, even cops with hacked TV in those days.
I grew up in Canada. Due to our close proximity to the United States and dimwitted TV programming, we have a long history of hacking US television signals going back to the big C band dishes of the 1980s. I farted around with this stuff as a kid but mostly just as a channel surfer. Eventually in the 90s the dishes got smaller (D band), and cheaper but they were now properly encrypted, which slowed pirates down initially – but not for long. After a series of cards and encryption methods were cracked a wave of illegitimate satellite use in Canada followed, which eventually escalated to somewhere around ~10% of all households having h4x0red satellite TV. Yes, seriously. I knew lawyers, clergy, even cops with hacked TV in those days.
So piracy is wide open in Canada at this time and I was lucky enough to know a few guys locally via IRC who were known in the online scene already. Most of the best testers were in IRC on Efnet or private servers in rooms like #DSS, #DSSHack, #DSSChat, #HackHU, and many others I’ve forgotten.
Signal hacking was hugely popular in the USA as well of course, but it was also very illegal there. O.J. Simpson famously got busted. Not so in Canada. That’s right, confusing the matter for many many years, Canadian courts refused to litigate on pirates and so signal hacking pretty much operated with impunity and was left to flourish. This all ended in April, 2002 when the Supreme Court of Canada ruled that U.S. grey market dishes were no longer legal in Canada. People were so pissed off they even tried to fight the ruling but this eventually failed. Oh shit, game over man. Right? Naaahhh.
Enter the DSS Tester
So what does this have to do with me? First, keep in mind I was in my early twenties when this all occurred and the internet was a lot more free in these years. Faced with the same situation today I never would have taken these risks.
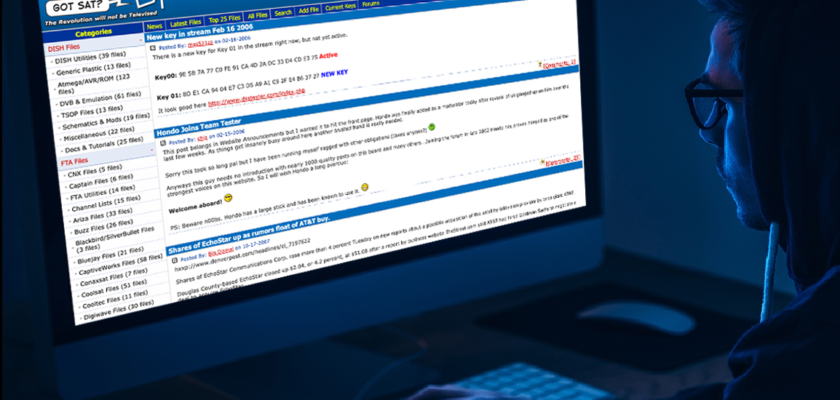
Having been a signal pirate for a few years now I decided to put up a website that shared 100% free information how to DIY this stuff. So in summer 2001 I started a DSS “testing” website hosted on my home cable modem that to my surprise almost immediately became incredibly popular. It was called DSSTESTER.COM. I was also openly programming 3M (fully open) cards for customers all over North and South America, but that ended when the Supreme Court ruling came out. The wayback machine is botching the design for some reason (below) but you can see the earliest post on DSSTESTER here: https://web.archive.org/web/20010720225051/http://www.dsstester.com/
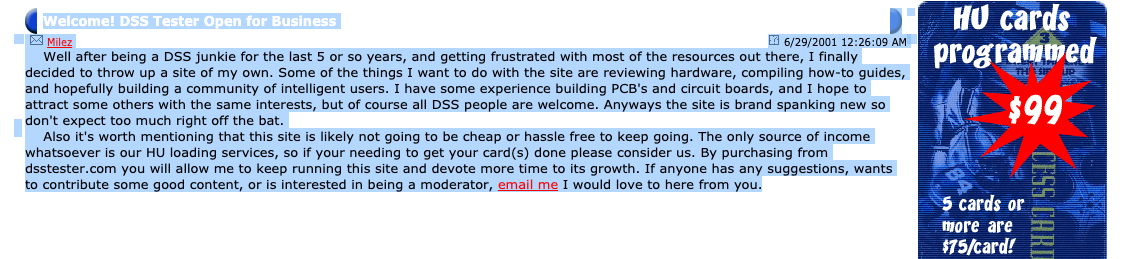
The DirecTV Era

X-Cube Emulator for H cards by DSSCanuck
If you like hacker lore the stories from this period will blow your fucking mind. I suggest you start with the Black Sunday Hack that looped the vast majority of H cards in January, 2001. This one really illustrates the game theory and cat and mouse game that was afoot here, and is to this day one of my all-time favourite DSS scene stories.
From 2000 – 20005 everything was aimed at DirecTV. The F, H, HU, were a series of cards DirecTV released that were all hacked to provide wide open programming (3M).
On the website traffic exploded so quickly I found myself moving to the best data center in Vancouver at Harbour Center. My bandwidth bills were approaching $2000/month but I was offsetting costs by selling banner space, working closely with hardware vendors, and programming cards for much of Vancouver.
It was a golden era of piracy and if you were active during this time you’ll remember elite usernames like: no1b4me, aol6945, and RAM9999. These guys signed their messages with PGP before it was trendy. So many legendary communities had been built: The Pirates Den (dsschat.com), Interesting Devices (id-discussions.com), DSS Underground (dssunderground.com), HackHU, Innermatrix, DR7.com, HitecSat, and too many more to mention. There were dozens of them and to my surprise DSSTESTER was quickly becoming a part of this pantheon.
I used to have Alexa data for this but to give you an idea, eventually at one point in 2006 DSSTESTER was in the top 2000 most visited websites on the entire internet. When TVs went down from an ECM I’d do millions of users in a weekend. The traffic was like an organic DDoS that never seemed to let up.

Above are logos used throughout the years and the Resources section from DSSTESTER in 2003

Mikobu Kick Ass Clones Glitcher from round 2002
But truly the reason traffic was exploding on the website, and to be frank the reason it was launched, is because the DirecTV HU card was hacked in early 2001, with 3M cards (fully open) starting to appear on vendor sites that spring. These initial HU loaders cost the first dealers tens of thousands and I was lucky enough to know one of them. I was programming cards for thousands of people right out of the gates before the general public could do so.
This didn’t last long however as someone released the source code for the atmel of the “HU Loader” on a website called HACKHU.COM. What this resulted in was HU loaders and eventually unloopers (used to program or fix cards) being sold for retail prices by a core group of mostly Canadian dealers.

File section from 2003 with our custom HU 3Ms
All throughout this period I am improving DSSTESTER and adding instructional tutorials and forum features to grow the community. We had an IRC server, a huge forum, encrypted email, a ton of tutorials, and generally a very friendly and libertarian attitude prevailed to everything. We also had some interesting ideas about things that are not so common today. If a satellite signal is being beamed onto my property from space, do I really not have the right to attempt to decrypt it? So edgy and esoteric but this was generally the consensus at the time in this scene. So much cypherpunk!

The Elvis HU Loader by DSS Canuck
Now it’s important to mention my focus and the reason we were successful was because our goal was to always be sure to keep things 100% free. Costs were funded by mostly private advertising, Google Adsense, and some merch sales, and the whole thing was run by a dozen or so dedicated volunteers. By 2002 our forum had exploded and I’d built a custom file database that was doing incredible traffic numbers. We eventually had private areas of the website too but the only way to gain access was to prove yourself worthy to the community by earning reputation points. Overall it resulted in a very strong community known for providing quality tested files and discussion about all manner of DSS esoterica.
But of course just when I was starting to be able to turn a small profit with this hobby and quit my shitty IT job, the courts had to go and make everything completely illegal. The last thing I wanted was for the RCMP to bust down my door. Hmm, but what if I wasn’t here?
I decided to see a Vancouver lawyer for a list of countries who wouldn’t extradite me to the US or Canada for running this type of op. She charged me $700 and produced a list. Right at the top was Malaysia. “Sounds tropical”, I thought.

Time to Make a Move
I moved to Kuala Lumpur in early 2002 carrying two Dell PowerEdge servers and whatever I could fit into some black duffel bags. I’d never been there before, and I must say that being here right after the Sept 11th attacks looking and talking like an American. It was a bit surreal sometimes.
In Vancouver I had a company auction off everything else I owned and send me a cheque (they ripped me off). In the weeks before I moved I was upfront about the nature of the website with many companies by email but the only ISP that would give me service was a scrappy startup called webservers.com.my. At the time they were just a few guys in a small office in KL. Today they’re probably Malaysia’s largest private hosting and co-lo provider with a huge footprint in the whole region. So they arranged to get me into Cyberjaya, one of the best data centres in SE Asia. I didn’t know it at the time but I wouldn’t be a resident of Canada again until late 2010. Here I am (on the right) loading my machines into a rack in 2002.

Now what followed is famous DSS hacker lore and was truly an epic back-and-forth battle between “testers” and Signal Integrity at DirecTV. It’s outside of the scope of this article but here’s a great thread someone did fairly recently that is accurate and really fun to go through. There is also a great History of DSS Hacking article by DSSTESTER member Vista which I posted recently here for posterity.
A thread about a small piece of hacking history – memories of the DirecTV “HU card” and the pirates that hacked the smartcard to watch free satellite TV.#tvpiratehistory pic.twitter.com/whYrdXAsV9
— Chris Gerlinsky (@akacastor) October 24, 2018
For a bit more detail you can also check out Steve’s recollections of this entire period as he is also on point.
And for the ultimate deep dive on the early days I highly recommend reading about Chris Tarnovsky’s history with NDS, and yes he’s the dude who wrote the Black Sunday kill – easily the baddest mofo in the history of the entire scene.
The DISH Network FTA Era
By late 2004 DirecTV had released their P4 card which basically ended hacking on DTV as it was never compromised. So this lead to a brief dark period where there was nothing to do but bitch and complain. Happily by the middle of 2005 the Nagravision 2 card from DISH Network had been dumped and it was back to business. The Nagra 2 cards were a huge improvement over the previous generation. These cards could support much more complicated math and had onboard cryptography coprocessors. Luckily someone had managed to glitch into early versions of them and this lead to a full dump of a card. This signalled a really interesting period whereby users used completely legal overseas FTA (free-to-air) devices by companies like Pansat, Viewsat, Coolsat, and reprogrammed them to decrypt the signal. It was essentially a feeding frenzy of free TV and if you were there you likely really enjoyed it.
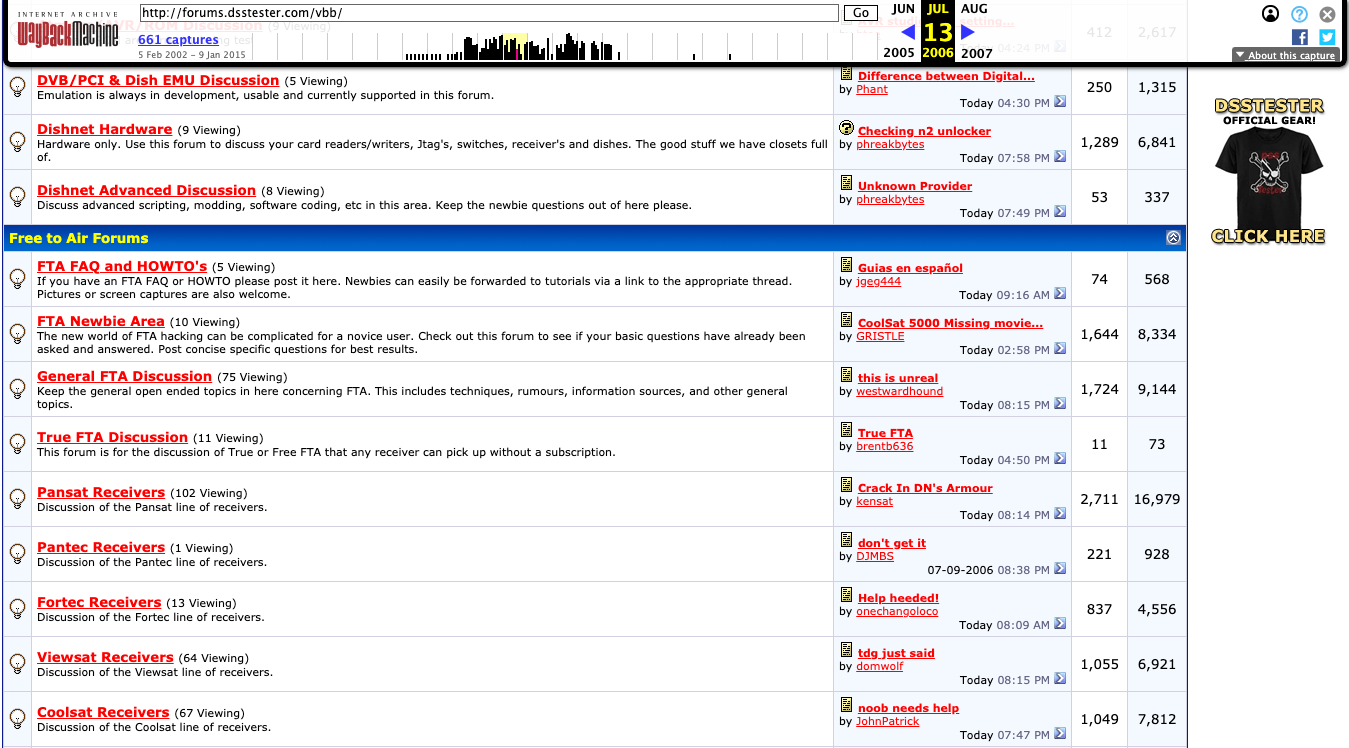
So now we have this very active period where the core DSS hackers (who were primarily hobbyists) are replaced by overseas, mostly Korean, shadowy actors who release code for their company’s FTA devices to drive sales. This change annoyed the hobby guys (us included) and many of them stopped contributing to the scene. Also during this period much of the larger community forums had been shut down by law enforcement. I had managed to forego this happening to myself by moving my operation overseas and being super careful, but I also knew eventually my number would be up.
I revamped our files section during this period and we quickly became one of the core places that released FTA files and fixes faster than anyone else. However by actually hosting the files I was taking some significant legal risks – and I knew it. Being worried someone would break my door down, even in Asia, was a daily concern.
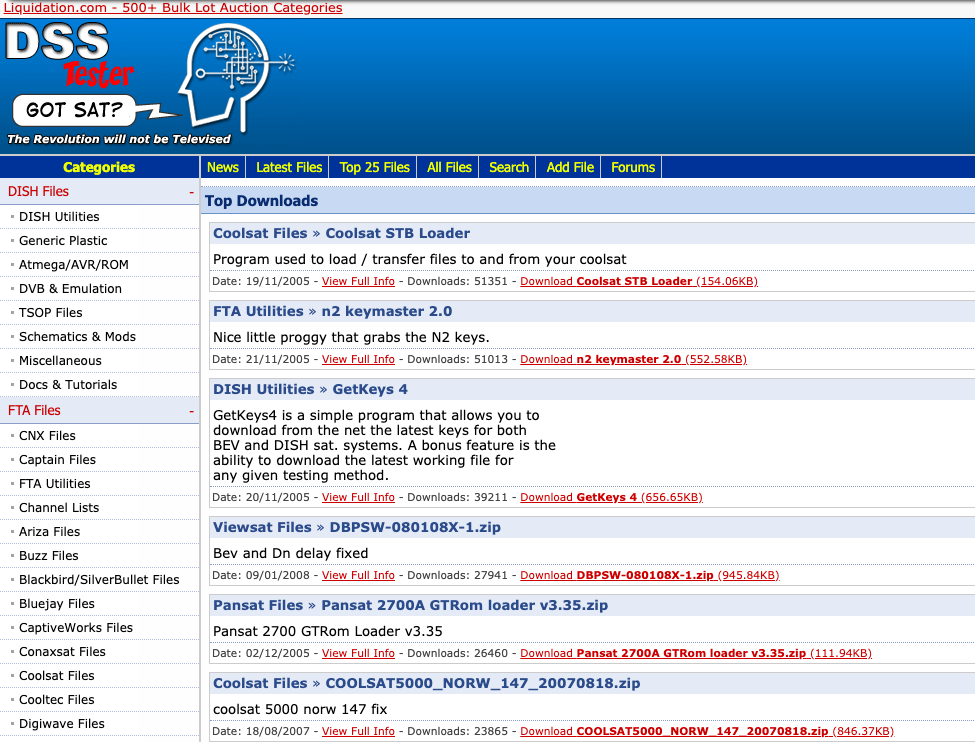
DSSTester revamped files section some time in 2005.
Some people I knew of or even worked with were put in prison during this period with long sentences and hefty fines. In the end most of these FTA companies were also eventually litigated against by DISH Network. Suffice it to say I was super paranoid as I had moved to Thailand which did have an extradition treaty with the USA. Little did I know I was on the radar by the guys at Signal Integrity around 2009 and was about to get a very scary email from Google.
Shit Gets Real
Okay now pay attention to how this unravels because you can learn an important lesson regarding how your online data works in the real world. One shitty day in 2009 I woke up to this strange email:
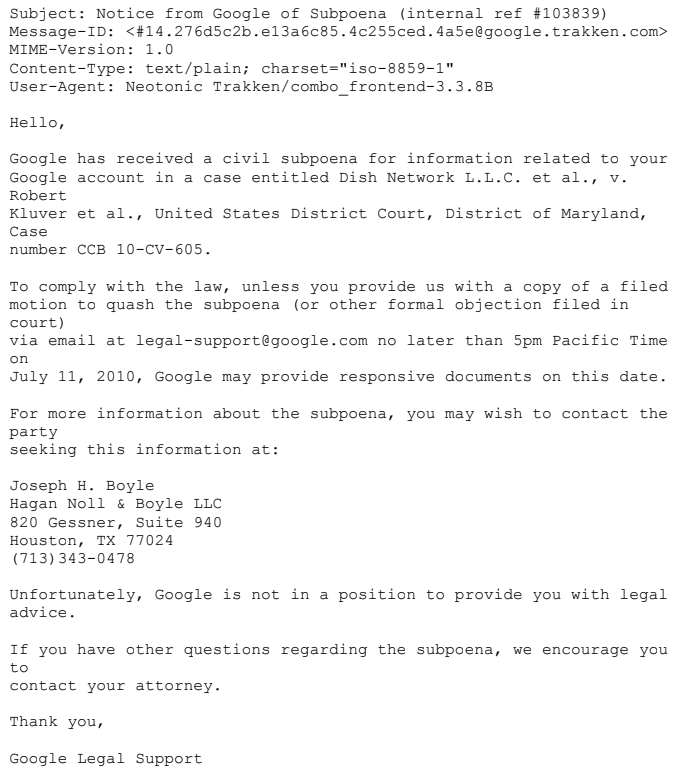
From 2000 onwards I always used encrypted email hosted on my own bare metal machines in overseas jurisdictions. Doing anything else would be n00b territory and I’d be in trouble fast. It was annoying and required constant maintenance but it allowed me to operate for years unimpeded. PGP encryption was also fairly common especially between specific people passing me sensitive files. I’ll also mention in the entire nine year period I ran DSSTESTER I was never doxed in any way, including to my friends on the website. There were plenty of attempts. Not to mention I had to deal with regular DDoS attacks, spear-phishing attempts, constant pen-testing and other nefarious shit.
 But as these things often happen I made one mistake on a lazy hungover Sunday during a beach vacation that got me rekt. DISH Network had noticed I had sold a banner to a person they were litigating against – the one time I used a stupid gmail account. So, I had to immediately hire an attorney or else Google would forward all of my info in 14 days. FUUUCK.
But as these things often happen I made one mistake on a lazy hungover Sunday during a beach vacation that got me rekt. DISH Network had noticed I had sold a banner to a person they were litigating against – the one time I used a stupid gmail account. So, I had to immediately hire an attorney or else Google would forward all of my info in 14 days. FUUUCK.
Now I wasn’t going to accept this fate because what they were doing was essentially a fishing expedition that resulted in a privacy violation. Even before I got an attorney I decided I would try to quash the subpoena on these grounds alone. As my lawyer put it: “Sounds like you could have a first amendment right to quash the subpoena”. Cool, let’s go.
Surprisingly, it worked! I think it cost around $7,000 but the subpoena was quashed and I was even mentioned in the court as John Doe. I remember hosting a huge party all that weekend in Bangkok to celebrate.
Tragically as I was soon to find out, none of this even mattered.
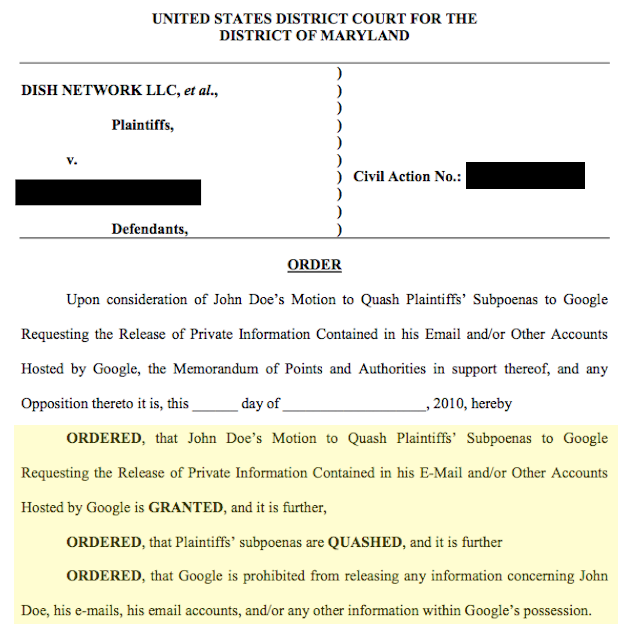
Okay it’s Time to Learn a Nasty Lesson
Now here’s the thing. Google was nice enough to let me know there was a subpoena for my account data but guess what? Nobody else even bothered to tell me. And by nobody else I mean: Paypal, eBay, 3 domain registrars, merch makers, VPN providers, and every other online service I had used with that email in the last five years. They had all been subpoenaed and happily handed it over without even letting me know and it works that way even to this day. DISH Network had sent all of this data over to my lawyer to show they meant business.
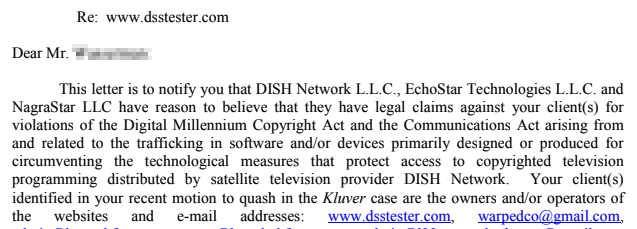
The amount of data, and the sheer detail of the metadata was incredible. Every IP, plaintext passwords, every transaction, times, dates, they had everything. But worse they had my identity, the prize, to me the only thing that even mattered.

Paypal’s legal department complying with the subpoena from Dish
So the gig was up, but I also knew the FTA scene was nearly dead anyways and wanted everything to just be over with. The only thing I really cared about was making sure myself and none of the volunteers who helped moderate, test files, and keep things operating weren’t going to have any problems. In the end this is exactly what happened and the big reason was because everything we provided was completely free without any form of pay wall.
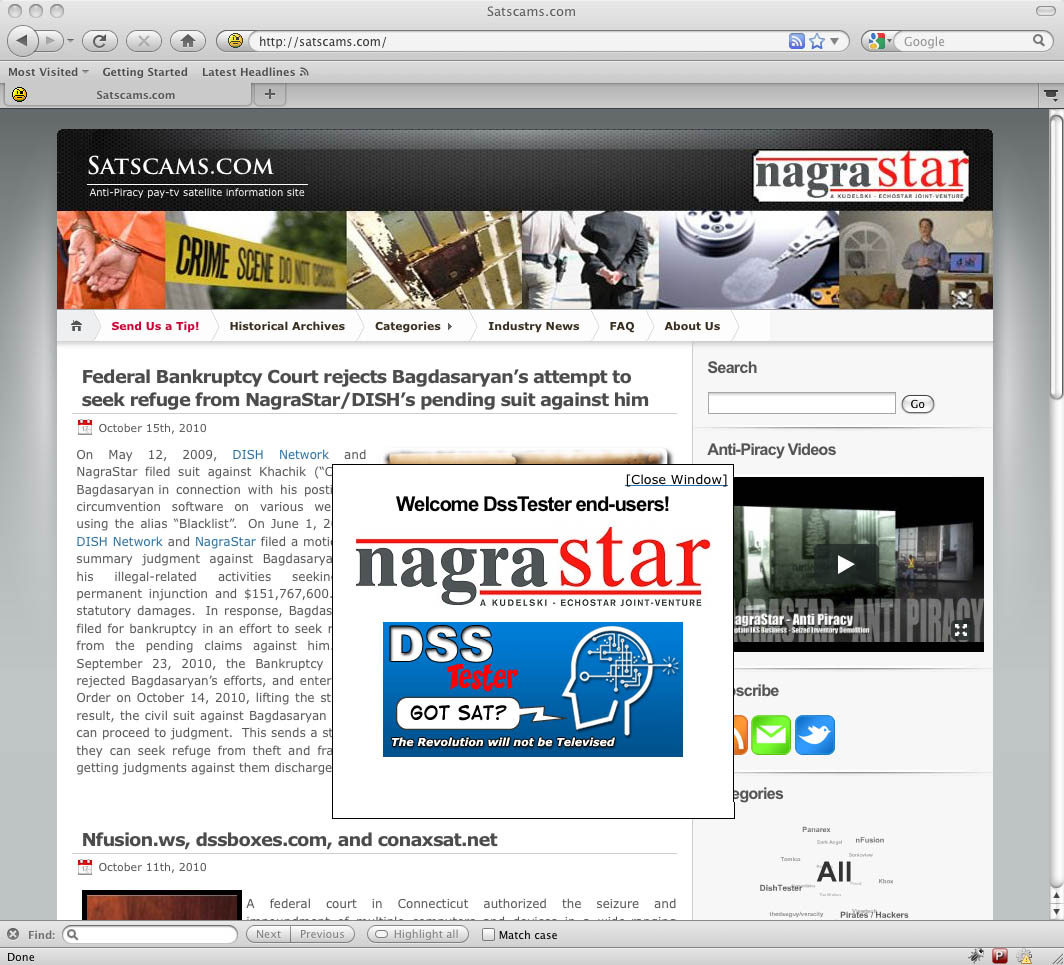
In October 2010 Dish took over my domain and forwarded it to SATSCAMS.COM
That said, originally I was threatened with some very serious fines. Jail time was very much on the table. $10 per download was thrown around as a fine and I had many millions of downloads. Other American citizens and even Canadians had been hit with fines like these and it had ruined their lives. Other guys got large jail sentences when they attempted to fight it in court.
So in early 2010 we started what became a 6 month process of negotiating an end to DSSTESTER. I am bound by this agreement to this day and will not divulge the details other than to say it ended with me ceasing all DMCA piracy related activities globally or I will face some rather heinous penalties. In the end I signed a non-prosecution agreement for myself and anyone who worked with me. DISH Network got the servers, and we both intentionally made very little mention of what happened other than my domain being forwarded to their enforcement website satscams.com (above). I’ll point out they didn’t ever ask about Apache log files, and I was relieved because I always send web access logs to /dev/null – even to this day.
To DISH Network’s credit they left me alone and I went on with my life. I was finally allowed to move back to Canada and this time I had a wonderful Thai wife to immigrate back with me and we’re still happily together today. The FTA hobby hacking scene died and was replaced by IKS / IPFS servers and other black market streaming services, mostly dominated by the Chinese today. I lost touch with most of the people from those days but I often think back how much fun we had sailing the high seas of 3M TV. One thing is certain, none of it would have been possible without their help, and I’m grateful to everyone who was there.
Shoutz: Frankie, HerbGreen III, Vista, Hondo, mas521ca, dbDan, Bobthetech, DssDude, and the dozens of others I’m forgetting. I often wonder what you guys got up to. Here’s a cypherpunk Wojak giving a thumbs up.

A Few Fun Facts in Closing…
I couldn’t possibly relay all the adventures that happened over such a long period but here are a few favourites:
- People often used pseudonyms to discuss the various providers: Dave (DirecTV), Charlie (DISH Network), Beverly (Bell Canada). Cute right?
- I operated DSSTESTER with multiple anon pseudonyms myself: milez, chip, SaintJames, and others.
- Once when I was concerned my location had leaked I convinced my entire userbase I lived in Singapore by timestamping a newspaper during a visa run there and leaking it. YES I was that paranoid.
- I was once sent $20,000 in cash inside a hollowed out VCR via Fedex for advertising services.
- I received a long series of death threats that scared the shit out of me over a period of years and I never told anyone. I spent many hours trying to figure out who it was but when I failed I bought a .45 cal Kimber Target II. Haters gonna hate.
- Google Adsense made millions serving ads on DSSTESTER over the years. I could never figure out why they didn’t pull my ads but I suspect it was because I held a large portion of their inventory. Ironically my biggest ad customers were the TV providers themselves.
- My servers were never compromised in the entire run of the website (at least that I know of) nor was my identity ever revealed. Always use 7 proxies.
I hope you enjoyed the nostalgia and I apologize this was so wordy. I doubt many people will read it all but it was definitely therapeutic writing it down finally. If you remember or were involved in the DSS hacking scene drop a comment below. I’d really love to hear about anything from this period as it’s just become so damn fuzzy over the years.
End transmission ツ