
First run Wildthing Unlooper from around 2001
The following article was originally written by Vista (Don Halbert), and posted on dsstester.com. If you were involved in the DSS / FTA hacking scene from the 1990s – 2009 you will remember some of this crazyness. In short, satellite signal hackers, or testers as we called ourselves, were involved in a cat and mouse game against television providers like Dish Network and DirecTV. Much lulz ensued.
At one point in Canada around the year 2001 it was estimated that 1 in 5 Canadian households had hacked (free) satellite TV from the USA. It was the national pastime. As someone who was there, I can tell you, it was a magical and fun time. Grab a coffee it’s a long but entertaining read.
—– snip
Originally written in 1999 and finished in 2001, I was the original writer of this article and felt it would be a good idea to reprint it in it’s original form.
The author of this article does not condone satellite piracy and any and all references to people, emails and links, have long been part of public domain. For entertainment purposes only!
The History of DSS Hacking
Shortly after release of the magazine article, the Canadian Battery Card made it’s debut and ever since then has caused DirecTV® to play keep up, trying to take out the Battery Card’s and their successors by sending ECMs or Electronic Counter Measures designed to effectively shut down the pirate cards and render them useless.
McCormac’s article began by telling how the Digital Satellite System was on the verge of being hacked and went on to say that the pirate’s would be releasing smartcards that would provide the owner of a DSS® system with access to programming through the use of an altered original card.
The article made mention of how signal pirates planned on making pirate cards available that would incorporate four tier’s with different programming options made available to the user. The first tier was to cost $150 and would provide access to only the basic programming. The second tier would add the subscription movie channels. The third tier would include the sports channels and lastly, the fourth tier would provide the user with access to all service’s as well as a $500.00 PPV credit.
There was actually no release of a tiered program that this author is aware of except for the one offered by the now defunct Cyber 1 operation based from the Cayman Islands. It has been rumored to be a scam, however, I cannot comment on the validity but will say that in the beginning it was the Battery Card that was being heavily distributed throughout Canada and not the plastic card as mentioned in the McCormac article. Plastic cards or original issue cards did not surface until later in the game and are now plug and play compatible and will work in any IRD (Integrated Receiver-Decoder).
Mr. McCormac says that the most valuable piece of information concerning the hack came from the smartcard itself and the text that is printed on the back of all card’s:
This card is the property of News Datacom Ltd. and must be returned upon request. Incorporates Videoguard(TM) security system. Provided for reception of authorized 101°W longitude satellite services. Protected by U.S. Patent 4,748,668 and others.
The patent that is referred to on the back of the smart card’s is known as the Fiat-Shamir or zero-knowledge test and is an authentication algorithm that is run by the decoder to check that the smartcard inserted is genuine. The authentication algorithm is the same one that is used in the analog Videocrypt system in Europe.
It was reported also that after the compromise of the Sky 07 card in early 1994, that the source code became widely distributed via the Internet and many BBSs(Bulletin Board System’s) throughout Europe. This was only month’s before the DSS® system was slated for release in America and I’d be willing to bet that DTV was shaking in their boot’s after seeing this just happen in Europe and where now wondering how long it would take before the American system was also compromised to the American best Hacker’s.
Not long after, the press began to tell of the new DSS® system, that was to be soon released, but they made absolutely no mention of what had happened in Europe. They did not mention the estimated 500,000 pirate Videocrypt cards and the Videocrypt emulator program’s that were in use.
All of this was in fact very real and had literally forced Sky to force a card reissue ten month’s ahead of schedule. It is said that the 08 card had to be scrapped because it was too similar to the Sky 07 and instead Sky opted to release the 09 issue.
The 07 and 09 cards went to a different algorithm as well as architecture. Sky started to distribute the 09 card in February of 1994 but did not switch to the new datastream until May 18, 1994. That day is known as Dark Wednesday by the European hacking community for obvious reason’s. The connection between those event’s and DSS is coincidental, but the timing is said to have been very convenient for News Datacom Ltd® to rely heavily on the design of the 09 card for the DSS® system, the main change’s would be made to the EEPROM where the cryptographic routine’s are stored.
Rumor has it that the 09 card took the European Hacker’s a few month’s to remove the code. It is rumored that the smartcard had been completely reverse engineered to dump the code. Some preliminary code was also sold at an auction in London in 1994 that may have given the hacker’s extra help. Approximately 4 month’s later the system was totally compromised. One of the most significant part of the operation was the discovery of a back door in the smart card’s code.
When the Videocrypt system was designed, the overall structure was simplistic compared with other system’s such as VideoCipher II, but it was thought to be reliable. and uncrackable. However, News Datacom apparently never imagined the customer base to grow so rapidly and had to implement levels of access control into the system. This was a good solution but also turned out to be very stupid and may be what started their very downfall.
The system News Datacom chose to implement, involved a method of programming the card’s over the air. The instructions that were sent looked liked a card identity number’s to the untrained eye. To the hacker’s they represented nanocommands or small commands and this was not good for News Datacom. This scheme that was once thought of as just so clever, but because the cards issuer had more control over the card and could issue ECMs (Electronic Counter Measure’s) and update the card’s EEPROM, which in turn would be able to change the channel authorization codes indicates now that it was a bad choice.
The downside to all of this is that that hacker’s could do nothing without the core algorithm of the card and a knowledge of the card addressing schemes. However they had already purchased part of the code at the auction and it was only a matter of time before it all came together.
Over time, the hacker’s slowly learned the function of each the commands and used it to there advantage. One command was found to read a byte from the EEPROM and input it as a round for the algorithm. Another was found that would act as a break command that could dump the results from the decryption key. The hacker’s had the main component’s for the DSS hack and only needed to put them to work and began by starting the algorithm from the first result and then stepping through with the input byte’s 0 to 255. This hack became known as the Vampire Hack in Europe.
The data that was first extracted did not appear to be related to the processor in the 09 card which is based on the 6805 microprocessor core until the hacker’s cracked the encryption scheme and it all began to make sense. It is rumored that the same technique’s described here were also use on the DSS 01 card issue.
In short it appears that News Datacom was aware of the potential security risk of releasing the same card for the DSS® ND upon it’s initial release. Now, it must now pay the ultimate price and will have to release a new card for the DSS® system. As far as I know, around the early fall of 1995 just after the Electronics Now® article, various dealer’s began offering the Canadian Battery Card which are also referred to as test card’s.
These card’s would enable anyone with a DSS® Digital Satellite System to get all programming offered on the system for a one time fee of approximately $700-$900 CDN dollar’s. This was a God send for many Canadian’s who had been denied the satellite programming by DTV (DirecTV)® as well as there own government. I effect saying that the dish did not provide the content that Canadian’s sought. Even stranger was the fact that the Canadian Government allowed the decoder box’s to be sold in Canada by dealer’s even though it was not legal for Canadian’s to purchase programming.
Go figure. The card’s enabled Canadian’s to effectively receive the programming they desired without having there own government make there programming choices for them. A government need not decide a man’s like’s and dislikes when it comes to television. Before these cards many Canadian’s had to rely on Grey market provider’s as well as redialer systems to get the programming they desired. The redialer trick did not take off too well and many people were disconnected after using them.
The Grey Market on the other hand continues to flourish in Canada and is it very simple to get a U.S. address to enable the programming. Many Canadian’s used this method as well as the battery card to obtain programming. A Canadian Judge made a ruling that you cannot steal what you can’t buy and such is the case with the DSS® Digital Satellite System. Canadians are allowed to buy the system or IRD (Integrated Receiver\Decoder) within Canada but we are not legally allowed to subscribe.
The cards have suffered many ECMs and each time they have returned with a new update and has been kept alive. There was also a split of the original engineer’s in the beginning that it, effectively, introduced two other pirate card’s: The L and T card’s that use the less secure Dallas 5000 to hold the master program.
On June 28th 1996, a massive raid was launched against some of the satellite dealer’s within Canada. It was not good and the following news report tells the details. Since this happened, the RCMP have been ordered by the judge in the case to return all properties seized from the defendants. Turns out the police seized property from many dealer’s that was not even related to the DSS card’s.
In coordinated raids in four countries, the bootleg smart card cops netted 26 people. Only 22, some of them Canadian, were named in a civil suit filed in Seattle, Washington and charged with the unauthorized reception of DirecTV and USSB. DirecTV said the raids were the result of a seven-month long investigation which was conducted coast-to-coast in Canada and the U.S. but also in Bermuda and Grand Cayman Island.
In Canada the raids were carried out by the Royal Canadian Mounted Police (RCMP). They obtained search warrants under Section 20 of the Canadian Radio communications Act. This section states in essence that it is illegal to sell, promote or possess a device that allows the unauthorized display of programming that is not distributed in Canada, or is owned by a Canadian distributor who has not been paid.
The raids took out several well known members of the hacker underground, including Norman Dick of Victoria, British Columbia. Mr. Dick is alleged to be the major inspiration behind the break of the News Datacom conditional access system that is used on the USSB and DirecTV signals. Dick’s nickname is Ground Zero. However, like the other Canadians named in the U.S. civil case, unless they are also charged in Canada, they may avoid the jurisdiction of the U.S. court by not traveling there because they will be listed as a fugitive from justice.
The same Norman Dick gained notoriety in hacker circles when he designed the Secure Universal Norm (SUN) board that was a knock-off of the General Instrument VideoCipher II decoder. Experts said the SUN was a cheaper and better design than GIs. For this Dick was also raided in 1988 and had over $150,000 worth of inventory impounded. An RCMP officer in Halifax, who refused to be identified, said they confiscated several of the bootleg cards in the raids and had gotten others in a sting several weeks ago when they bought bootleg cards to obtain the evidence for search warrants.
Another source said one defendant bought a new truck with $60,000.00 cash and this alerted authorities. The RCMP refuse to say if there will be charges filed in Canada. Fines are up to $100,000.00 on each count for a corporation. Also notorious in the hacker underground in Canada is another two defendants, Doug and Troy Stewart of Nanaimo, BC, Gary Tocholke of Victoria, BC, Ron Ereiser of Kerobert, Saskatchewan, Karen Bradford of Westmount, P.Q., Kevin MacMillen of Woodstock, N.B. and Bill Mitten and Ron King of Halifax, N.S. In a strange twist, Mitten, King and McMillen are not named in the Seattle case. In the same press released DirecTV said it will begin a full card swap in August.
Shortly after the raid’s the Battery card seemed to be lacking support and the original programmer who was writing the main .enc file’s needed by the battery card was under such heavy surveillance by the Canadian R.C.M.P that he could no longer support the battery card without causing himself more trouble’s in upcoming court case’s, shortly after the battery card’s incurred a downtime of about two month’s because NOBODY had the skill’s to produce files for the battery card or cared not too.
During this downtime it is known that a European engineer, with the brain’s to accomplish the feat, entered the scene and literally saved the battery card. Since the arrival of the Big Gun, he has won the support of battery card user’s throughout North America as well as providing a new bootstrap named the V3 that is performing perfectly at this time. Not much is known to the public of Big Gun, only that he is the person that provides the file and obviously knows the system well and was the ONLY support for the battery card at that time. Other’s have claimed they have the skill’s, but none have proven the way the Big Gun has.
It should also be noted that the renowned hacker, AXA, has provided support time and time again for the L-card as well as the T-card and the old bootstrap. The L-Group who originally made these cards has been long gone for some time now and has left there customers high and dry and have left many end users without support had it not been for the intervention of the AXA as well as the occasional help from the BG.
AXA deserves many thanks for all his help also. AXA had the I System which is an L card which has been modified and has the atmel chip removed and therefore the I-system card after conversion looks very similar to the battery card. Other systems in use include the Emulator systems released by Pierre aka (PGM) as well as various plastic software released by authors such as Tornado and Castor.
The P2 Datastream
On Monday June 23, 1997, a day which some call “Black Monday” Directv and News Datacom implemented the P2 datastream. Directv had been sending new access cards out to subscribers for over a year. The new card, dubbed the P2 or “H series” was developed to increase security of their conditional access system. The original P1 or “F series” card had been fully hacked, with many different cards available, some available for free. The P2 card looked similar to the old one, however it had been significantly designed internally different. Along with nearly doubling the EEPROM memory, it now had a intel-based internal Siemens processor, rather than the Motorola based processor that the F series had. This cards claim to fame however was the addition of another component called an ASIC, or Application Specific Integrated Circuit.
Several hackers had been working on cracking the EEPROM of the new card for some time now. One of the major problems that the F series hacks had was that they could not duplicate the Motorola processor perfectly, so they had to emulate it with an intel based one. This difference was one of the reasons that the cards were ECM’d so often. Another reason was that the software was often freely released on to the internet. Once released to the masses via the internet, its open season for DTV and NewsDatacom. So the processor problem was good news, however they still had to “dump” the EEPROM (Electronically, Erasable, Programmable, Read, Only, Memory) and extract the microcode out so they could begin on a testing solution.
Some of the developers of the F series cards such as AXA seemed to have underestimated the security of the new cards, as they expected to have the answer within a couple of weeks. There were several major problems. 1) Capital. Reverse engineering is very expensive, costs can easily soar to over $100 000. 2) Technical Knowledge. The developers had experience compiling bootstraps, however they lacked the technical experience or equipment to extract the microcode from the EEPROM, so it was necessary to send it to an outside lab in most cases. 3) Cost Effectiveness. The ASIC was a big problem. It was soon discovered how the ASIC worked, however because it was application specific, it was not available on the market and it would have to be manufactured from scratch. The cost of such a venture would be formidable.
Over a month and a half had passed since the datastream was switched, and AXA and other developers still had nothing. At this point we saw the emergence of the East 3M card. The 3M developers had begun the project of dumping the code a lot sooner than the others and so they had a big head start. Because they used the P2 access card, the ASIC problem was solved. The initial cards were quite expensive, most were selling for $500 US+ . Because of the extensive code modifications, many people were hesitant of paying such a large amount for a card that could go down at any time. They were counting on the other developers to come through with a less expensive option.
But it was not to be, at least not right away. The combination of talents from AXA, PGM and Tornado proved to be insufficient against the security of the P2. Over 2 months had passed and they were not able to dump the EEPROM. Without it, a solution would not be possible. More and more people had been giving into the temptation of having no TV and were purchasing the 3M card in large numbers. Shortly after, a new 3M card was developed in western Canada. This would be dubbed the West 3M. Many people were hoping that the competition would cause the prices to drop significantly. They did not. Prices came down slightly and settled around $400 US.
For about 2 months, the East and West 3m cards were the only options available and sales flourished. Then a new option was introduced. It had no official name, but soon came to be known as the Combo Card. However the price was very high, up to $650 U.S. A lot of dealers were claiming that it could not be ECM’d and so many were sold. Shortly after a new knock off product known as the DDT was introduced. The price was still high, but less expensive than the combo card. Both the Combo card and the DDT worked in conjunction with a P2 access card. The major difference was that the combo card would work with a virgin, unactivated access card and the DDT required a small subscription in order to work. It had now been over 5 months since he datastream switch, no ECMs had occurred.
The first ECM occurred on November 21, 1997. It was targeted against the 3M cards. It was speculated that a member of the East 3M group has sent in a copy of their software after making a bunch of money and leaving the group. This is where some interesting things happened and the East group lost a lot of their popularity. Both the East and West 3M cards were ECM’d with a massive 99 loop, causing the cards to lock up and be neither readable or writeable. Almost immediately, the East 3M group issued a statement claiming that the cards were not able to be repaired and they required the user to pay $100 US plus send in their old card. Many people were enraged about this as they were promised free support. What enraged people most however was that the West 3M group was claiming that the cards could be fixed. The west group’s offer was a lot more appealing. They offered to reprogram a new card for $50 Cdn.(cost of new card) and the user would have the old card returned when repaired, or the user could wait and receive a FREE unlooping and reprogramming. Further they also offered to extend the offer to East 3M customers except they would keep the old access card. New software was available about 2 weeks after the ECM and most people who paid the $50 were playing within a month. Many were holding off for a free unlooping as it looked promising that a solution would be found. The initial unlooping was not entirely successful. The first attempts were engineered by Eddie from North Sat Technologies in Winnipeg, Manitoba. They first attempted to glitch it out of the 99 loop by applying low voltage to the card. Some cards were fused permanently. After some tinkering, it seemed that they had it, it was unlooped and they could now read the card, they were sent off to be tested for reprogramming. It was soon found that they could not be written to however and so it was necessary to try again. About a week later North Sat was successful and he began to unloop cards and send them on to the programmer. The sheer number of cards proved to be the Achilles heel as only so many cards could be reprogrammed in a day. Most people were playing again with unlooped cards 2 months after the ECM.
So things slowly began to return to normal. Some new cards began to emerge. Most were constructed by non-programmers looking to make a quick buck. The DDT card had been dumped and people were selling the software to virtually anyone that wanted it. A flurry of new products meant that prices would come down, it also meant that a lot of people were selling cards that they had no hope in supporting. There were still only a few people capable of writing a program. Most of these cards were copies of the DDT card.
A new card called the DAT emerged among the copies. The DAT had similar appearance to the others, it also had a packet generator and a blocker built in. The DAT was hacked and cards such as the BOSS emerged. With no hope of writing a software patch themselves, copies of the mainstream cards relied on the hopes that if the cards were ECM’d, that the developers of the mainstream cards like the combo card would release a patch which then could be copied.
The ECM happened on January 15. 1998. The target was old 3m cards that were still being sold for low prices, and all the wedge cards. The combo cards and DDT cards were specifically targeted and many DDT and Combo card users had their P2 cards 992d. DTV had begun a major code write to their cards in the hopes of closing the security hole which allowed the wedge type cards to operate. The hole was dubbed the “093 hole. Cards that were written to or “updated” by DTV would no longer work with the wedge cards. A few cards were spared. Although not immune to the update procedure, they were put on to life support due to the blocker that was built into some cards, like the DAT. The blocker would block the updates and allow the card to continue to operate. Cards without initial blockers now had to add them to their cards and they needed a new virgin access card in order to make them work. Around this time some freeware “Activation” software was released, such as CBA or CL5005. These programs would activate the tiers on a new virgin access card and allow normal programming minus the PPV to be viewed in the open. These cards were limited to 25 PPV. A non virgin card could not be programmed with this software.
The wedge cards and 3m and some of the activation programs were ECM’d again on March 27, 1998. Directv had previously been sending regular access card updates through the 42nd packet. Wedge cards were effectively blocking these updates. Cards that did not block it were down as it patched the holes which the cards were using to turn on the channels. Directv now began sending 5 new updates through the 40th packet, one that blockers were not designed to block. In some wedge cards, these 5 new updates would turn off the dynamic tiers (PPV) and the regular channel tiers would continue to run as long as the first 18 updates were being blocked. On some other cards, all channels were down. 3M West and 3M East were both being 992d and being deactivated due to some updates interfering and corrupting the 3M software in the card. Directv would now be in a position to 99 any cards that were not updated if they chose to. Some of the newer programs were not affected, such as the Blazer, 4M and some newer versions of the West 3M and SuperV.
Shortly thereafter the West developed the Wildthing! unlooper. This unlooper was designed and engineered by a fellow out of Bulgaria. This unit could do cards that normally took up to 20 mins in Eddie’s unit in seconds. There has never been a finer unlooper to date than the Wildthing! Now, the Wildthing! unloopers are duplicated by almost every DSS related site on the internet. The unloopers have gone from Wildthing!, to Wildthing! 2, and finally Wildthing! X.
October 6,1999 there was an ECM directed at one of the more popular freeware programs available. Known now as the Oct.6 Magic ECM. This ECM damaged the jump table and fuse bytes within the card. Many people underestimated DTV and shrugged it off that a fix would be available asap. Well time will tell us that this didn’t happen. Throughout Oct. no one had a solution for this ECM. Finally, in November, Eddie at Northsat developed a repair for this ECM. His repair involved the cloning of all cards with a good image. His success rate was rather shady and slow. The unit did the job but not exactly efficiently. End of December the Wildthing! 2 was released. This unit repaired Magi and Euro ECM’d cards in seconds like it predecessor the Wildthing! Finally a unit for the masses.
Now today’s status of the P2 has taken a turn for the worse. H cards are now very difficult to find due to DirecTV’s move in issuing the P3 or HU card with new systems. And if you intend on subscribing to an H card you better check again as DTV will tell you to courier your H card to them and they will courier you out an HU or P3 card. Unfortunately, the only way you are running wide open viewing right now is if you apply the CAM ID of an actively running subscribed card and then 3M it. This is currently the only way to avoid the “7453 issue unless you choose to run freeware spoofing software which uses F card CAM ID’s. These freeware spoofer files are not lasting long so the best is to get yourself and active sub image and 3M with your flavor of the month 3M.
The P2 is so wide spread that literally everywhere on the net or next door, someone is hacking it. Freeware is running wild with the P2.
Leading up to the fateful day, DirecTV had been regularly updating their cards, which had the entire hacking community confused as to why and why so regularly. Well…
Like the final piece of a puzzle, the final updates made all the useless bits of computer code join into a dynamic program, existing on the card itself. This dynamic program changed the entire way the older technology worked. In a masterful, planned, and orchestrated manner, DirecTV had updated the old and ailing technology. The hacking community responded, but cautiously, understanding that this new ability for DirecTV to apply more advanced logic in the receiver was a dangerous new weapon. It was still possible to bypass the protections and receive the programming, but DirecTV had not pulled the trigger of this new weapon until…
January 21,2001 the H card users got the shock of a lifetime. Once again, DirecTV ECM’d the cards damaging the memory range 8000, which is the write once, area of the card rendering them useless. This day was dubbed “Black Sunday” and caused many pirate viewers to stare at a black screen for the much anticipated Super Bowl the following Sunday.
Some estimate that in one evening, 100,000 smart cards were destroyed, removing 98% of the hacking communities’ ability to steal their signal. To add a little twist to the operation, DirecTV personally “signed” the ECM. The first 8 computer bytes of all hacked cards were rewritten to read “GAME OVER”.
Just when DirecTV thought they had successfully accomplished their mission of eliminating the hacking community a solution was found. The hacking community succeeded in developing a “boot board” which emulated the damaged 8000 area of the card and acted like a protector or sheath. Now the hacking community was back on track for only suffering a bit of a delay. To date, June 2002, these “boot boards” are still in operation.
The most important factor is that people should realize that the P3 will NOT be hacked via some basement hacker and then offered for free on the net. If you believe that it will happen outside a lab then you best be reading this story again. Nope, we expect the P3 hack to come from a commercial source who can afford to pay the engineers required to dump the processor. Once commercial 3M is being loaded for a few months then maybe, only maybe, the lesser expensive alternatives will arrive. Of course they will time has shown us this game before.
PART 3 – The New Horizon
Early in November of 2001 there was much ado about an apparent hack for the P3 or HU card. People claiming it was a sting or a fraud were everywhere. The original dump of this card was performed in a Russian laboratory funded by a fellow known for arranging the sale of the Magic ECM glitch points to Triton. Don represents Brian, the brains behind the coding. Brian took the dump from the Russian engineers and developed the first program for HU cards labelled HUPro. This file was built off original code from Triton, which exchanged hands in the sale of the Magic glitches. Thus the likeness in appearance. The following months saw dealers from Winnipeg and Ontario loading HU cards with HUPro. In a very short time trouble began to stir within the group and rumors of inside corruption began.
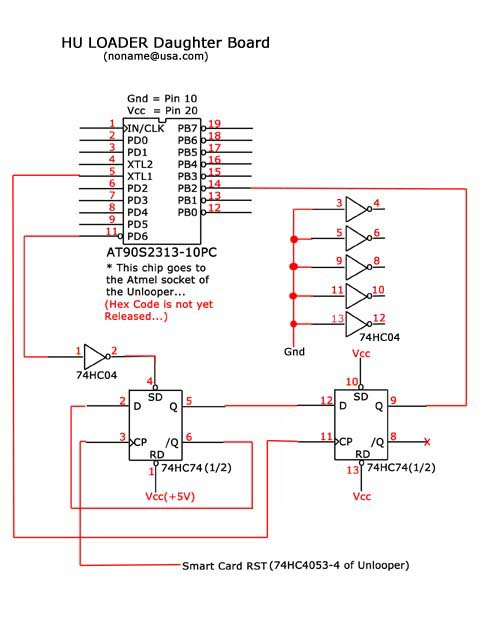 In January, a few dealers began to advertise “HU Loaders” for sale. Behind the scenes what originally occurred was this…
In January, a few dealers began to advertise “HU Loaders” for sale. Behind the scenes what originally occurred was this…
Brian and Don decided to sell the technology. Now between them they decided that Triton would never have this technology nor would they sell it to them for reasons still yet unknown. So they sold their wares to a fellow nicknamed JT who at the time owned a website. JT reportedly purchased the product for a large sum of cash and returned to the states to begin marketing his new product. And at the tail end of January, JT began selling the “HU Loader”.
Within a week of JT marketing his product Triton began marketing the same product for a considerable less amount of money. For weeks many people doubted Triton had anything to sell meanwhile collecting pre orders for sales of the item. The original loader device was shipped by Triton to the UK and completely reverse engineered and dumped by Cambridge engineers.
By the end of February Triton released the Wildthing! Piggyback chip for current loaders. This chip combined with HUPro would allow users to program HU cards. Within three weeks after the release of the piggyback chip purchasers found themselves with another bonus, the Wildthing! XS the world’s smallest unlooping device to hit the streets.
On March 11,2001 a website released the source code for the Atmel on the “HU Loader” on the net. This infuriated many as they had just paid thousands for their devices and suddenly someone releases it for free on the Internet. This stunt was completely orchestrated by Don and Brian to potentially damaged Triton’s reputation in a vengeful attempt at getting back at them for dumping their code.
With the mass market on sites selling H and HU products DirecTV decided enough was enough and began an anti hacking campaign within the United States. They successfully shut down operations of many US based web sites and prosecuted many individuals involved in the hacking or assistance in hacking of their property. War was staged.
By March 2001, many dealers were beginning to advertise HU3M options to their clients for sale. With the public release occurring so quickly on the loader people began questioning where they would get 3M support from. Thus the market saw an opportunity and seized it. Soon plenty of sites were offering script support for HU3M files. The first ECM on HU cards occurred on January 23,2001 and the following on March 29,2001. This second one was anticipated by many due to the release of the atmel code and source for HUPro. Both ECM’s looped thousands of cards. In early April 2001 “Eddie” formally of NorthSat began unlooping HU cards. For many months he monopolized on this technology until March 18, 2002 when an individual nicked “unatester” released the unlooper code on the Internet for FREE before any dealers had any hope of recouping their investments.
During the hacking melee another storm was brewing. Rumors of former hacking personalities rolling over on their peers, turning leaf and working for DirecTV/NDS, and the biggest rumor of all…NDS responsible for the release of the hack on their competitor’s smart cards, Nagravision.
In filings connected to its lawsuit on News Datacom, Canal Plus identified Von as Chris Tarnovsky, the NDS employee. Von, also known as “Big Gun” or BG, was mentioned earlier in this writing. Tarnovsky, like Floricic, the now infamous deceased hacker, was an expert in smart card technology who lived in Germany until he was recruited by NDS and became an employee of theirs living in the United States. Reportedly on March 26,1999, Von released Secarom.zip on DR7.com unleashing a wave of conspiracy theories and immense scrutiny aimed at his employer NDS.
[editor: Tarnovsky ended up revealing all as evidenced in this Wired article from 2008]At any rate, with the secret codes to both NDS and Nagra smart now public, the playing field in the smart card business was level. By August of 1999, NDS had a new four-year contract with DirecTV. HoweverPsychology Articles, the contract contained an important escape clause — that DirecTV could develop its own in-house smart card technology and dump NDS at any time. Well they did just that in April 2002 and now there is the release of the NEW series smart card for DirecTV systems…the P4.
Enjoy and happy television!
Compiled with information from various sources to numerous to mention
Vista



