At the end of July, 2020 Ledger the French company behind some very popular crypto hardware wallets made a news post detailing a data breach they had suffered. In their update they admitted to losing customer data including the home addresses, emails, names, and phone numbers of 9,500 users.
On the surface it didn’t seem so bad but the crypto community went ape shit over this news as many of us suspected the breach was far worse than Ledger claimed. A growing number of users in the /r/ledger subreddit complained of phishing attacks and SMS based scams. A lot of people lost money to these scams and as time went on it became obvious there was more to this leak than met the eye.
I like to keep an eye on leaks like this so I had been waiting for a drop on the forums where this stuff usually happens. On Dec 20, 2020 Twitter user (@UndertheBreach) tweeted about a thread on Raid Forums (archive link)
ALERT: Threat actor just dumped @Ledger's database which have been circling around for the past few months.
The database contains information such as Emails, Physical Addresses, Phone numbers and more information on 272,000 Ledger buyers and Emails of 1,000,000 additional users. pic.twitter.com/Sv9cQwhuNy
— Alon Gal (Under the Breach) (@UnderTheBreach) December 20, 2020
Here we have a user by the handle Burgulema111 giving away Ledger customer data for free. This was a bit unusual as the data is quite valuable and they could have easily made some good money selling it. Most likely it was already for sale somewhere and this user was just passing along the goods for some clout. I’m not really sure yet.
But what was more surprising was how much data the download contained.
Inside Ledger.rar are 2 files:
- All Emails (Subscription).txt – 1,075,382 records
- Ledger Orders (Buyers) only.txt – 272,853 records
Here’s a breakdown:
[Ledger Orders (Buyers) only.txt] Email Provider Stats: [gmail.com] 139,930 (51.3%) [hotmail.com] 23,250 (8.5%) [yahoo.com] 16,565 (6.1%) [protonmail.com] 4,880 (1.8%) [outlook.com] 4,259 (1.6%) [gmx.de] 3,411 (1.2%) [icloud.com] 3,390 (1.2%) [web.de] 3,236 (1.2%) [aol.com] 2,491 (0.9%) [me.com] 2,311 (0.8%) [Other] 69,195 (25.4%) TOTAL: 272,918 [All Emails (Subscription).txt] Email Provider Stats: [gmail.com] 587,403 (54.6%) [hotmail.com] 84,231 (7.8%) [yahoo.com] 60,531 (5.6%) [outlook.com] 14,615 (1.4%) [protonmail.com] 13,117 (1.2%) [icloud.com] 10,555 (1.0%) [aol.com] 9,433 (0.9%) [gmx.de] 9,123 (0.8%) [web.de] 8,297 (0.8%) [mail.ru] 8,134 (0.8%) [Other] 269,892 (25.1%) TOTAL: 1,075,331
Wow that’s a lot more data than Ledger admitted to, just as we suspected. So Ledger either:
- Knowingly downplayed the breach and underreported the data loss
- Unknowingly misreported the breach because they didn’t understand its severity
Either possibility is obviously very troubling.
Don’t Trust Verify – Download the Data Yourself
- One of the original upload links the RF leaker provided is: https://anonfiles.com/Day5W603pd/Ledger_rar
- I provided some links on twitter but they keep being taken down so here’s an anonymous torrent that will remain seeded: LINK 1 | LINK 2
- Magnet link
- If you don’t want to risk a download you can also search at intelx but you are rate limited to how many times you can search without signing up. Good enough for a quick check: https://intelx.io/?s=0b6c44ff-0c94-46c4-b8ad-b7cb762ba5c6
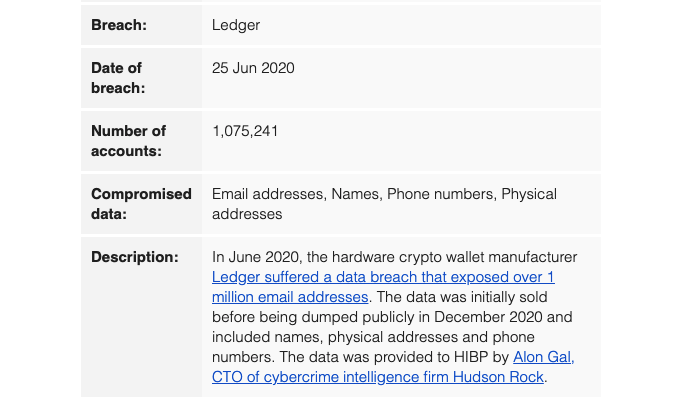 I wanted to avoid writing this article but there has been some difficulty over people accessing the data, and some confusion over the two data sets. To make it worse tools like haveibeenpwned are reporting to ALL users that their names and physical addresses have been leaked even if their email only appears in the big email list.
I wanted to avoid writing this article but there has been some difficulty over people accessing the data, and some confusion over the two data sets. To make it worse tools like haveibeenpwned are reporting to ALL users that their names and physical addresses have been leaked even if their email only appears in the big email list.
They really should have released it as two data sets but I guess they have some obscure reasons as to why they didn’t bother.
Heaps of reasons I’ve detailed to death many times in the past including massively increased processing overhead, fundamental schema change and ultimately, the goal of @haveibeenpwned to report on presence in a breach which it does with already
— Troy Hunt (@troyhunt) December 21, 2020
In the end Troy mentions they released it as one breach because it was just easier that way ¯\_(ツ)_/¯
Because there was one breach. Imagine if, for every breach in @haveibeenpwned I had to start breaking single incidents apart into smaller ones based on who had which data attributes exposed. Nightmare. Easy solution: ask Ledger what data was exposed, that’s their responsibility.
— Troy Hunt (@troyhunt) December 21, 2020
I’ll point out that the reason I’m making this available is because it is important Ledger users see it. Criminals already have it so there is no point staying quiet about it. I also really don’t like when people lord over this type of data and responsible disclosure is uber important these days, so here we are.
Horror! I’m in the breach what now?

If you found yourself in this breach here is what I would do:
- Use a different email address. Now. You can forward emails from old -> new but label them so you know their origin.
- Get a new phone number and think hard about any services you gave this number to, especially those that still use SMS for 2FA, like Google. If you can afford it you can keep the old number for a few months and tell anyone who calls or TXTs your new number.
- In future use a PO box for any sensitive shipments like this. A UPS store will do this for $5 per shipment here in Canada.
- You should also use a throwaway email and fake name for sensitive shipments.
- Your home may not be a safe place for your seed phrase if you are in the addresses list. You should consider a different place to keep this unless you move to a new address.
I hope this helps alert those who were affected by this and that is my only motivation for providing the files. At the end of the day everyone who was impacted by this has a right to know what was leaked.
In the future always remember that privacy and security are two sides of the same coin. Without one the other doesn’t exist.




you probably gona get sued for that…. always VPN?
That’s not how this works. When data like this is leaked it becomes a part of the public domain. I had nothing to do with the breach or originally leaking it.
Hi there,
There does not seem to be any seeders of the torrent files you have linked – is this something that can still be seeded for a bit?
The list is virtually impossible to get anywhere.
Thanks!
@Tom: It’s working here, try the magnet link again.
Thanks @gr3y : I got it downloaded in the end. Really appreciate you guys for the content and support! Take care
Hi again guys, curious if this list includes the additional 20,000 records leaked recently as per this article: https://cointelegraph.com/news/ledger-owners-report-chilling-threats-after-20k-more-records-leaked
If not, do you have any leads on how to get a hold of this?
Thanks guys
@Tom: Nope doesn’t include these. They have not been leaked/sold to my knowledge but I could be wrong. If anyone finds them please drop a link and I will add to this post.
Thanks for the reply, much appreciated!